Blog
How to Simultaneously Achieve Identity, Operational Resilience, and Third Party Access Management Goals with Exostar Access: One
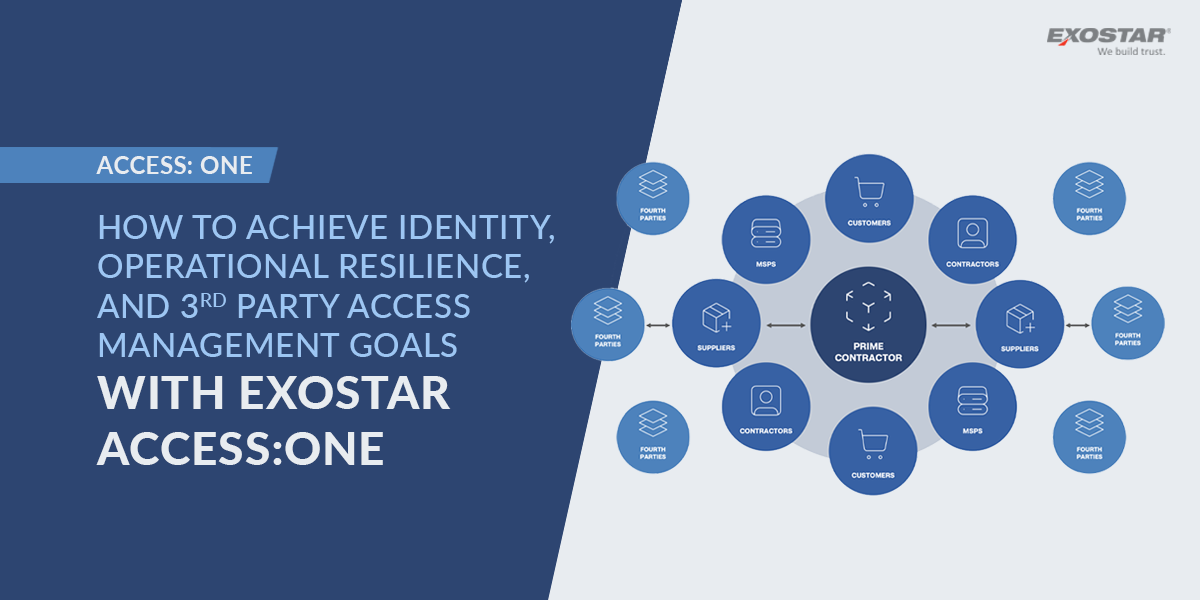
In a world where cyber threats are on the rise, organizations face complex challenges when protecting sensitive data – especially in highly regulated industries. Recent research highlights that the cost of a data breach can soar upwards of 10 million dollars and supply chain attacks are even more expensive and difficult to fix, causing cost to go up by 11% or more
Keeping Collaboration Safe and Efficient
While collaboration is key to business success, the distributed nature of supply chains –involving global, multi-tiered ecosystems of suppliers, partners and other third parties – can make them vulnerable to cyber-attacks.
Recent regulation, such as the Digital Operational Resilience Act (DORA) and Australia’s CPS 230, provides valuable guidance regarding how to reduce risk when collaborating within complex supply chains. Alongside this, new technology (for example, third-party access governance tools), further reduce the risk associated with opening your network to business partners, customers and other third-parties. Through best practice supply chain access management, organizations can be better prepared and protected against the risk of a data breach.
When considering cross-organization collaboration, it’s important to consider how you securely manage digital identities and their access to enterprise applications and data to prevent cyber threats.
A holistic approach to digital identity can reduce the risks associated with opening your network to suppliers, business partners and customers. A strong Identity and Access Management (IAM) solution, such as Exostar Access: One, will help you succeed in keeping data safe without disrupting collaboration.
Implemented well, your approach to digital identity will ensure a consistent set of policies, processes and technologies which manage and control an individual’s access to digital resources. IAM’s primary goal is to ensure that the right people have the right level of access to the right resources at the right time, all whilst ensuring high levels of security and compliance with minimized risk.
Securing Your Supply Chain with Exostar Access: One
Access: One provides a comprehensive set of capabilities which support digital identity, operational resilience, and the management of third-party access. The platform provides capabilities focused on n-tier security which ensure consistent controls and the protection of sensitive data throughout your organization’s ecosystem of employees, customers and partners (even throughout your supplier’s supply chain). With Access: One, your entire supply chain will benefit from increased visibility and security.
When using Access: One to secure third-party access:
USERS can easily authenticate and access all their applications through a secure portal. Password-less authentication and self-service ensures users are productive and secure from day one.
LINE MANAGERS can easily administer team member access and perform delegated actions on behalf of their team. With continuous controls such as access certification, line managers can be confident the right people have access to the right systems with an appropriate level of privilege.
ADMINISTRATORS can easily define and administer security policy whilst managing user access across all protected services from a single point. Administrators can delegate security tasks to sub-organizations, ensuring that management is performed locally to the user and by those administrators responsible for each organization’s security.
From workforce and partner identity to consumer access management, Access: One enables resilient and versatile services for access management, administration and governance. Delivered as a service, Access: One is a turnkey solution to enable highly regulated organizations to provide secure IAM services to employees, partners and consumers.
Learn more in our white paper, Identity, Operational Resilience, and the Management of Third Party Access, about the role digital identity plays in securing the supply chain and how third-party access governance helps reduce risk and comply with relevant regulation.